Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!
In this article, you will learn a variety of techniques that will allow you to regain access to your computer. We will start with the most simple and archaic of methods, then progress to more complicated and robust ones.
Warnings
- Use this information in a responsible manner.
- Do not use on computers you are not authorized to use.
- Check if encryption/decryption software is legal where you live.
- We are not responsible for anything you may or may not do with this.
Step 1 Win-XP Backdoor
Tip
- If you are running something newer than XP, which is likely, then skip to the next step.
When you log onto a Windows XP machine, you will typically be greeted with an icon which you click to log on, called the "classic logon". We don't want this:

We want something like this:
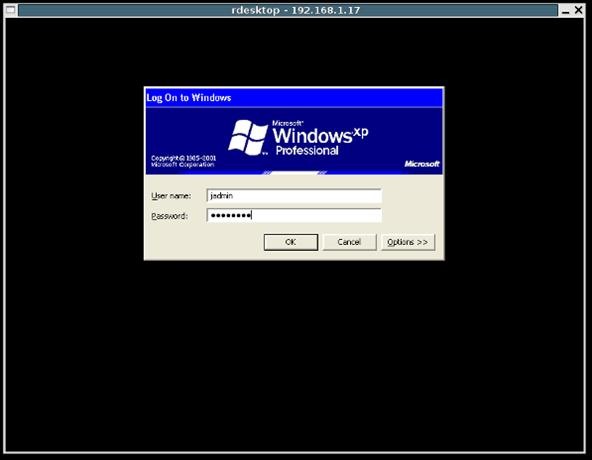
We can switch to this log on screen by pressing "ctrl+alt+del" repeatedly on the classic log on screen.
The default User name and Password are typically: {"Admin", "admin"}, or some variation of these (e.g. "Administrator"), respectively.
If you can't seem to gain access, which is fairly likely, especially if you are running something other than XP (since most newer Win-OSs don't have this backdoor), then move onto the next step.
Step 2 Keylogger
Tips
- If you are not computer savvy or simply malware paranoid and don't mind a bit of espionage, then skip to step 3. Come back if all other methods fail.
- Also be aware that many antivirus programs will see this software as malicious, so don't be surprised if that happens.
Another option that is pretty simple, is to install a keylogger. You can usually find a semi-reliable one on CNET (just search for "keylogger"). Make sure to read the reviews and user-ratings and whether it is free or not. Keep it simple, we aren't trying to dig up someone's whole personal life (well, you might be, but that's your business). Free and simple things usually work best in my experience.
After you install it (pray it hasn't done anything too psychotic to the computer), it will probably give you a secret series of keystrokes you need to push to bring up the keylogger, make sure to memorize or write it down somewhere safe. Also, make sure you activate the keylogger. It would be a shame if you "snuck" on the computer and then you didn't log anything!
Now you just have to wait until the person who knows the password comes on the computer and enters in the password you want. Once they have, sneak back on the computer and pull up the keylogger and search the logs for what you want. Knowing a time period when they entered it may be helpful for this part. And voilà, hopefully you will have got what you wanted!
Afraid someone will do this to you?
Look into getting an "online screen keyboard", that forces you to click a keyboard on the screen so that the keystrokes are never logged. I will try making a tutorial in the future that expands on prevention of keyloggers, but just be wary of what software you install and be familiar with what processes are running in the background of your computer. Also, if you want to go all out, there is actually hardware that functions as a keylogger that you place between the keyboard cord and the computer; just search around on eBay/Google. Wireless keyboards could also theoretically be intercepted, but I haven't contemplated in depth exactly how that could be done.
Step 3 Cain & Abel
This is probably the most effective, simple piece of software that I have seen around, for password acquisition! You can download Cain & Abel here. The only downside is that I don't recall there ever being a Linux version, but then again, the software specifically targets Windows systems most of the time.
How do you use this to gain the password?
Simply install it, which may be slightly difficult if your antivirus doesn't like it, such as with the keylogger, which is probable. After that, simply run it, then click on the "LSA secrets" -> "+" and it will ask you some stuff about getting it from the hive or local machine, etc. You should be able to just click "next". Then, it will automatically dump all the password hashes, decrypt them and display the plain text!
In my experience, this works best with XP. I have had difficulty with other operating systems. I grew up hacking XP computers, so sorry if you are still yelling: "I don't want to get into an XP system!" Don't worry, the next step should hopefully cover that.
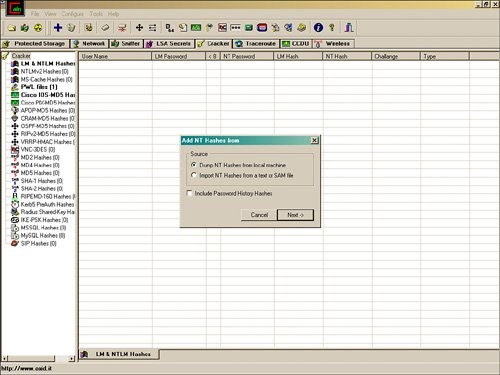
Tips
- Check out the other features of this program, such as the network sniffing utilities or decryption tools! They are fun to play around with. :)
Step 4 Ophcrack
Okay, if none of the other methods have worked, then this one probably will! It is one of the more complicated ones, but it typically has a higher success rate, especially if the computer you are trying to get on had a crappy password.
What you need to do is download Ophcrack.
You can go down two different alleys for this:
- Live CD
- Direct Installation
Essentially, you always want to go through the Live CD way unless you have unlimited access to the computer. I have it installed on my computer, just so I could see if I could hack my own password. You may actually want to try this out and familiarize yourself with the software prior to using it on another computer.
Download the software and then prepare it to be burned to a CD, but do not do it quite yet, there is more to do. Another alternative, is to put it on a flashdrive, which is what I did because I don't have many CDs lying around. For a tutorial on doing this, click here.
What you also need to do is download and extract any rainbow tables that you want to use. Rainbow tables essentially contain an organized table of all the possible hashes that exist given a certain set of characters (e.g. uppercase letters, lowercase letters, special, etc.), which is much more efficient since you don't have to compute the hashes when you are cracking. Based on the suspected maximum length and type of characters of the password on the computer, you need to select the appropriate table (see the Ophcrack download page). If you are on Windows 7, then use the Vista tables, they should be sufficient. After you have downloaded a table, then place it/them in the "tables/" folder on your CD.
Burn the CD and you are almost all ready!
Simply insert the CD into the computer and restart it. You may have to call up the boot menu by pressing F12 or something, but it may automatically boot from the CD/USB drive you inserted. Next, the Ophcrack Linux distro will boot up, which takes about a minute. Then you simply select the passwords you want to crack and click "start"... and hope for the best! Some passwords are cracked in 3 seconds and some take an hour—it really just depends on the password length and randomness (and of course, if you selected the most efficient rainbow table).
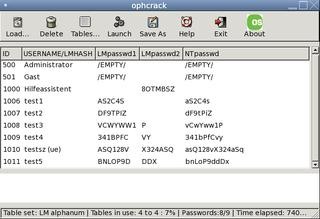
I have had times when I could simply not crack using this method, but it works most of the time. If not, I resorted to more surreptitious espionage methods as in Steps 1 through 3. Where there is a will there is a way, as I always say! :D
Just never give up. Keep trying. Keep learning, researching, asking questions until you find your answer! Nothing is impossible unless you believe it is. :)
- Stay tuned for more Invisible Computer articles and how-to's!
- Follow us on Google+ or Facebook!
- Questions? Idea for a new article? Visit our Forums!
Just updated your iPhone? You'll find new Apple Intelligence capabilities, sudoku puzzles, Camera Control enhancements, volume control limits, layered Voice Memo recordings, and other useful features. Find out what's new and changed on your iPhone with the iOS 18.2 update.


















7 Comments
Nice trick. Very well explained. Thanks!
This is a great walk through. Nice job mate!
Thank you, I am glad you liked it!
Thank you.
If the computer is only windows password protected and unencrypted, just download put any linux distro like puppy or ubuntu on a usb or dvd. Then edit your boot order settings to boot from the usb or dvd drive.
Yes, assuming the hard-drive is unencrypted, booting from CD is not disabled and there is no BIOS password, then you can access their data with ease using a Live Linux CD! I just wrote this how-to under the assumption that you want to gain actual access to their Windows account without altering the password (there are also plenty of password recovery programs, but that removes the password entirely, thus alerting the person of someone tampering with their computer).
The best method is using KonBoot..
Share Your Thoughts